Cybersecurity 202: Staying Secure
Cybersecurity is a term broadly referring to the process of protecting computer systems, networks, devices, and programs from cyberthreats. Industry and society increasingly rely on tech and internet solutions to conduct day to day operations. The first three months of 2020 saw a 20% increase in cyber fraud as cybercriminals took advantage of the global pandemic. Maintaining security protocol and preventing data leaks is a central practice to any modern organization.
Data Breaches Vs. Data Exposure
Data Breach – Planned cyberattack on an organization’s database.
Data Exposure – Caused by human error such as inadequate information security.
Google Disfavors Unsecured Sites
While many factors contribute to a site’s search engine optimization (SEO) strength, website safety and security status is an undeniable contributor to a site’s likelihood to appear at the top of a search engine results page (SERP) Google’s search engine algorithm detects corrupted websites and effectively places them lower on the (SERP) – a direct hit to a business’s overall SEO. A secure website is a more efficient lead generator and representation of your company’s reputation.

Data at Risk
To visualize the economic, reputational, and regulatory impact a data leak may have on your business, here are examples of stolen information that a hacker will abuse:
| Customer Info | Company Info | Trade Secrets |
| Personal identity information | Internal communication | Plans, Formulas, Designs |
| Order & Payment History | Performance statistics | Code & Software |
| Browsing Habits & usage details | Projects & other collected data | Commercial Advertising Data |
| Credit card information | Critical Contact Information |
Primary Victims of Data Breaches
In 2020, there was a reported 156 million data leaks nationwide with an average cost of $133k to companies with less than 1000 employees. The relevance or popularity of a website does not make it more prone to a data leaks, even small businesses must maintain cybersecurity standards to prevent information breaches. Websites the most at risk for a hack will always be websites managed under poor security policy (SP).
Any strong cybersecurity procedure involves routine and comprehensive security policy.
The Rising Popularity of Cloud Infrastructure
At a rapid pace, enterprises are making the shift to internet “cloud” storage to host servers, services, data and more. Some of the major cloud providers include Amazon Web Services (AWS), Google Cloud, IBM Cloud and Microsoft Azure.
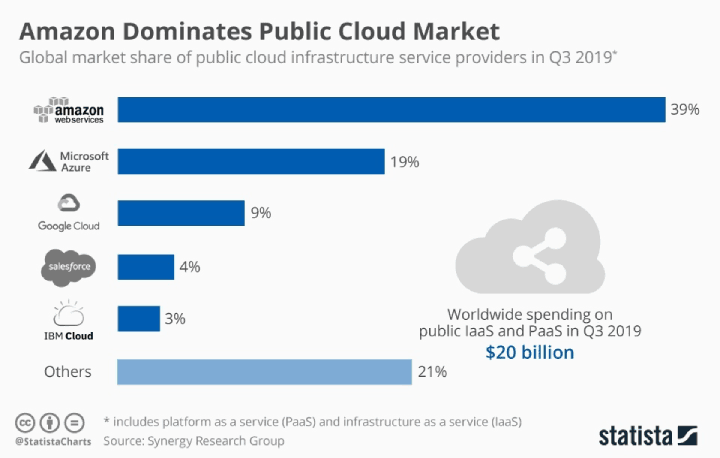
There is strong value in cloud storage, primarily in the operational advantages that allow resources to be automatically distributed across vast and geographically varied servers – a capability that traditional computing did not serve.
The Reality
Despite the rising popularity of cloud-based services, even the world’s largest companies have been victim to major security-hacks. According to a report by Cybint, 95% of cloud security hacks are caused by human error. Notoriously, internet storage platforms are programmatically breached due to its security system complexity and cloud migrations. Industry experts suggest that incident response plan testing and continuous comprehensive security protocol can greatly reduce the likelihood of any type of security threat.
Risk Prevention
Like a piece of kitchen equipment, a website must undergo regular maintenance to promote efficiency, especially as its use increases. As a software development and digital marketing agency, Beedash recognizes the clear-cut necessity to uphold succinct and best-practice security standards to support our dealer partners.
Have a Request for a New Feature?
Feel free to let us know at anytime which features you’d like to see in Corestack Product Information Manager. You can submit a feature request using our Corestack Service Desk’s Feature Request form linked below.


